Other Entra ID / Azure AD SignIn errors
The challenge
Most of us analyzing Azure AD SignIn logs have been there. You come across a failed sign-in, but the ResultDescription is not really helpful, but only shows “Other”.
When using the Entra ID portal UI most of those error codes will perfectly translate to a more helpful error message.
So how can you have the same experience when using KQL?
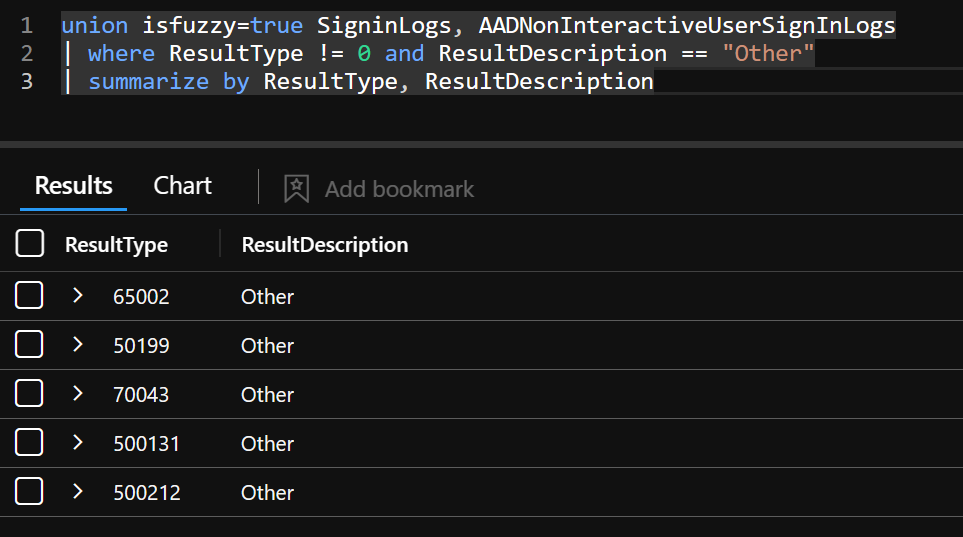
First things first, let’s analyze which unresolved error types are in your environment.
union isfuzzy=true SigninLogs, AADNonInteractiveUserSignInLogs
| where ResultType != 0 and ResultDescription == "Other"
| summarize by ResultType
Based on this data you can do two things:
- Lookup the error code in the UI
- Use the official reference Azure AD Authentication and authorization error codes to lookup the error code
- Lookup the error code using the sign-in error lookup tool
Option #3 is the best of the three, because I don’t want to lookup hundreds of error codes manually and the official website does not cover everything you are looking for.
The way to the solution
Since the error code website by Microsoft has a super simple interface which is easy to parse, I created a small script that does the heavy lifting for me. Since I also didn’t want to miss any error codes I might not have in my initial list I also don’t just check the exact error message id, but also 20 error codes up and down the original error id. This way I checked a total of 2143 possible error messages. Of course some are invalid and others might already be resolved in the Sign-In logs. Of those 2143 checked error codes I was able to get 764 unique error messages which I saved as a JSON file.
And voila, now I can lookup the missing values right in your kusto query using the externaldata function.
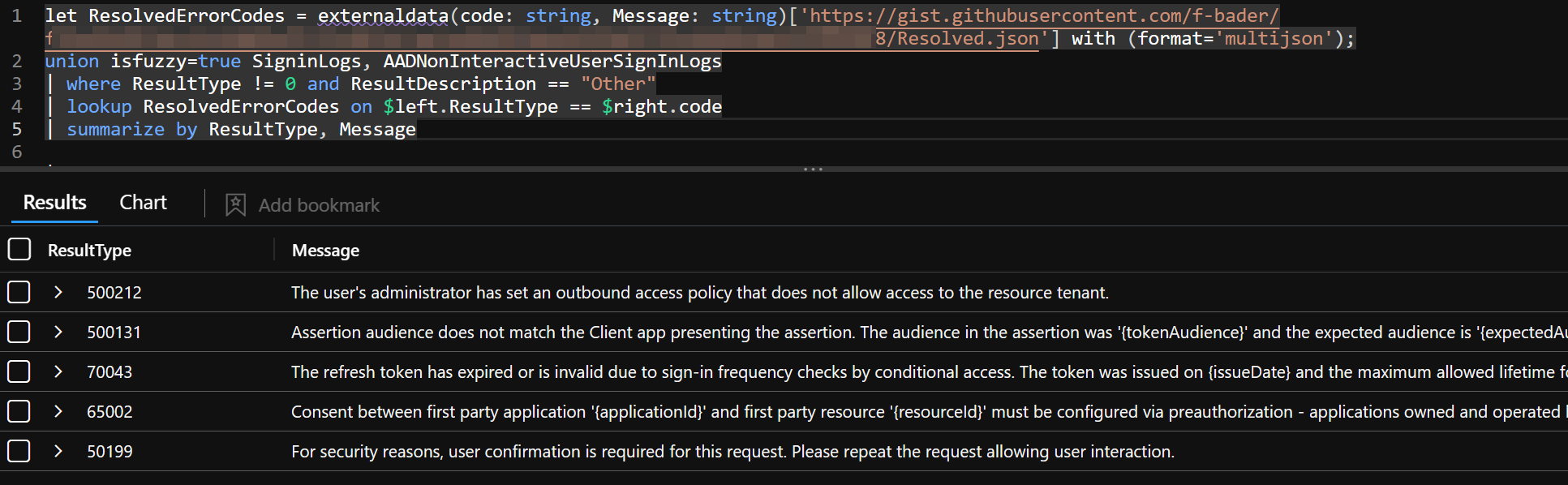
Since I want to keep the original format of the Sign-In logs I added a another line to replace the original ResultDescription if the value is “Other” and the lookup table contains a better description.
let ResolvedErrorCodes = externaldata(code: string, Message: string)['https://raw.githubusercontent.com/f-bader/EntraID-ErrorCodes/main/EntraIDErrorCodes.json'] with (format='multijson');
UnifiedSignInLogs
| where ResultType != 0
| lookup ResolvedErrorCodes on $left.ResultType == $right.code
| extend ResultDescription = iff(ResultDescription == "Other",iff(isempty(Message),"Other",Message),ResultDescription)
| project-away Message
| project-reorder TimeGenerated, ResultType, ResultDescription

The solution
But always querying external data might not be the most performant way of doing this. A Sentinel watchlist should be the better solution for this.
UnifiedSignInLogs
| where ResultType != 0
| lookup _GetWatchlist('EntraIDErrorCodes') on $left.ResultType == $right.SearchKey
| extend ResultDescription = iff(ResultDescription == "Other", iff(isempty(Message), "Other", Message), ResultDescription)
| project-away Message, *1
| project-reorder TimeGenerated, ResultType, ResultDescription
For your convenience, I created a ARM template you can use to deploy a watchlist.
I uploaded all this data to a new GitHub repository where you can consume it as JSON, CSV or find the ARM template to deploy the watchlist directly.
Entra ID - Azure AD Authentication and authorization error codes
| ResultType | Message |
|---|---|
| 26000 | The provided access grant requires interaction. |
| 29200 | QR Code requested. Generate QR code and display on UX page for interactive sign-ins. |
| 29201 | Invalid QR Code request. Client Id ({clientId}) or target client Id ({targetClientId}) is invalid. |
| 29202 | Invalid scope and response_type request parameters. scope=qrcode can only be used with response_type=none. |
| 29203 | Invalid target_client_id ‘{targetClientId}’ argument value. |
| 29204 | Failed to write QR Code token to Store. |
| 29205 | Generated QR Code string has exceeded maximum supported length. |
| 29206 | Invalid QR Code redemption request. Client Id ({clientId}) is invalid. |
| 29207 | Error processing session data. QR Code is either invalid or expired. |
| 29208 | Error processing session data. QR Code was already redeemed. |
| 29210 | QR Code sign-in is disabled via user credential policy. |
| 29211 | QR Code sign-in is not supported for passthrough users. |
| 29212 | QR Code sign-in is not supported for consumer user scenarios. |
| 40002 | The identity provider returned an error. The status returned was ‘{status}’ and the message was ‘{message}’. |
| 40003 | A required token was not emitted by an external Identity Provider. |
| 40004 | A required token was not emitted by an external Identity Provider. |
| 40005 | Invalid token received from external Identity Provider. Current time: {curTime}, expiry time of assertion {expTime}. |
| 40008 | There was an unexpected error from the external identity provider. |
| 40009 | The identity provider returned an error. |
| 40010 | The identity provider has failed with a transient error. |
| 40013 | Social IDP MicroService Federation disabled. |
| 40014 | Federated Identity Provider is unavailable. |
| 40015 | The identity provider returned an error. |
| 40016 | The Identity Provider returned an error. |
| 50000 | There was an error issuing a token or an issue with our sign-in service. |
| 50001 | The resource is disabled or the resource named could not be found. This can happen if the application has not been installed by the administrator of the tenant, or if the resource principal was not found in the directory or is invalid due to a typo. |
| 50002 | This tenant isn’t supported for this authentication method yet. |
| 50003 | Certificate roll is in progress. Please retry the operation later. |
| 50004 | A transient error has occurred. Please try again. |
| 50005 | User tried to log in to a device from a platform ({platform}) that’s currently not supported through Conditional Access policy. Supported device platforms are: iOS, Android, Mac, and Windows flavors. |
| 50006 | Signature verification failed because of an invalid signature. |
| 50007 | Encryption certificate was not found in the directory. |
| 50008 | The SAML token is invalid. |
| 50010 | Audience URI validation failed since no token audiences were configured. |
| 50011 | The {redirectTerm} ‘{replyAddress}’ specified in the request does not match the {redirectTerm}s configured for the application ‘{identifier}’. Make sure the {redirectTerm} sent in the request matches one added to your application in the Azure portal. Navigate to {akamsLink} to learn more about how to fix this. {detail} |
| 50012 | Authentication failed. |
| 50013 | Assertion failed signature validation. Possibly because the token issuer doesn’t match the API version within its valid time range, it’s expired or malformed, or the refresh token in the assertion is not a primary refresh token. |
| 50014 | The user’s redemption is in a pending state. The guest user account is not fully created yet. |
| 50015 | The user requires legal age group consent. |
| 50016 | Invalid Argument Redirect ErrorCode value. |
| 50017 | Validation of given certificate for certificate based authentication failed. |
| 50019 | This occurred due to an interrupt to select a certificate before the user signs in. |
| 50020 | User account ‘{email}’ from identity provider ‘{idp}’ does not exist in tenant ‘{tenant}’ and cannot access the application ‘{appId}’({appName}) in that tenant. The account needs to be added as an external user in the tenant first. Sign out and sign in again with a different Azure Active Directory user account. |
| 50023 | ClaimType ‘{claimType}’ is reserved for system use. |
| 50024 | Unable to decrypt client state. |
| 50025 | The issuer name must be specified. |
| 50026 | The mail is too long, maximum length is {length}. |
| 50027 | JWT token is invalid or malformed. |
| 50029 | The reply URI specified in the request contains invalid characters. Domain names of this form are not supported. |
| 50030 | Either forwardableOnBehalfOfOriginsAcceptedAudiencesList or ForwardableOnBehalfOfOriginsAcceptedPrecedingAppsList property in the first party app registration is not set. Both fields need to be filled on first party app portal for PFT OBO to be successful. |
| 50032 | RSA key size {actualSize} is less than the minimum required {minSize} bits. |
| 50033 | A transient error has occurred. Please try again. |
| 50034 | The user account {identifier} does not exist in the {tenant} directory. To sign into this application, the account must be added to the directory. |
| 50035 | ECC key size {actualSize} is less than the minimum required {minSize} bits. |
| 50038 | The API version isn’t supported. |
| 50042 | The salt required to generate a pairwise identifier is missing in the principal. |
| 50043 | Unable to generate a pairwise identifier with more than one salt in principal. |
| 50045 | The salt required to generate a pairwise identifier is malformed in principal. |
| 50048 | Subject must match the issuer claim in the client assertion. |
| 50049 | Unknown or invalid instance. |
| 50050 | The request is malformed: invalid format for ‘{name}’ value. |
| 50051 | The root key endpoint is missing the root keys. |
| 50052 | The password entered exceeds the maximum length. Please reach out to your admin to reset the password. |
| 50053 | The account is locked, you’ve tried to sign in too many times with an incorrect user ID or password. |
| 50054 | Looks like you entered your old password. Try again with your new one. |
| 50055 | The password is expired. |
| 50056 | Invalid or missing password: password does not exist in the directory for this user. |
| 50057 | The user account is disabled. |
| 50058 | Session information is not sufficient for single-sign-on. |
| 50059 | No tenant-identifying information found in either the request or implied by any provided credentials. |
| 50060 | Unable to sign out. |
| 50061 | Unable to complete signout. The request was invalid. |
| 50062 | Signout request is unauthorized. |
| 50068 | Signout failed. The initiating application is not a participant in the current session. |
| 50069 | Signout failed. The request specified a name identifier of ‘{identifier}’ which did not match the existing session(s). |
| 50070 | Signout failed. The request specified session indexes ‘{identifier}’ which did not match the existing session(s). |
| 50071 | Signout request has expired. |
| 50072 | Due to a configuration change made by your administrator, or because you moved to a new location, you must enroll in multi-factor authentication to access ‘{identifier}’. |
| 50074 | Strong Authentication is required. |
| 50075 | The tenant ‘{tenant}’ does not have security defaults enabled. |
| 50076 | Due to a configuration change made by your administrator, or because you moved to a new location, you must use multi-factor authentication to access ‘{resource}’. |
| 50077 | The administrator created a conditional access policy that requires the authenticator to be used to provide GPS location. |
| 50078 | Presented multi-factor authentication has expired due to policies configured by your administrator, you must refresh your multi-factor authentication to access ‘{resource}’. |
| 50079 | Due to a configuration change made by your administrator, or because you moved to a new location, you must enroll in multi-factor authentication to access ‘{identifier}’. |
| 50080 | Bad request received. |
| 50081 | The administrator created a conditional access policy that requires GPS location. |
| 50082 | The partitioned token signing key endpoint is missing the partitioned token signing keys. |
| 50085 | Refresh token needs a social identity provider login. |
| 50087 | A transient error has occurred during strong authentication. Please try again. |
| 50088 | Limit on telecom MFA calls reached. Please try again in a few minutes. |
| 50089 | Authentication failed due to flow token expired. |
| 50091 | Passed query string length exceeds supported limit. |
| 50093 | Missing value for the SAML NameID. |
| 50094 | Unknown source configured on the audience for the SAML NameID. |
| 50095 | Unknown source configured on the audience for the SAML email claim. |
| 50096 | Source configured on the audience for the SAML NameID is not compatible with the requested format. |
| 50097 | Device authentication is required. |
| 50098 | JWT body must contain ‘{field}’. |
| 50099 | Invalid nonce. |
| 50100 | There was an error transforming the claims for the token. |
| 50101 | Unknown claims transformer ‘{name}’ was specified for principal ‘{principalId}’. |
| 50102 | Unable to load CustomClaimsTransformer ‘{type}’ was specified for principal ‘{principalId}’. |
| 50103 | There was an error transforming the claims for the token: {errorMessage} |
| 50105 | Your administrator has configured the application {appName} (’{appId}’) to block users unless they are specifically granted (‘assigned’) access to the application. The signed in user ‘{user}’ is blocked because they are not a direct member of a group with access, nor had access directly assigned by an administrator. Please contact your administrator to assign access to this application. |
| 50107 | The requested federation realm object ‘{name}’ does not exist. |
| 50120 | Unknown credential type, issue with the JWT header. |
| 50123 | Unknown claims transformation method ‘{method}’ was specified for principal ‘{principalId}’. |
| 50124 | Invalid regular expression configured for claims transformation for this application. |
| 50125 | Sign-in was interrupted due to a password reset or password registration entry. |
| 50126 | Error validating credentials due to invalid username or password. |
| 50127 | Client app is a MAM app and device is not registered. |
| 50128 | No tenant-identifying information found in either the request or implied by any provided credentials. |
| 50129 | The device is not workplace joined. Workplace join is required to register the device. |
| 50130 | The claim value(s) ‘{value}’ cannot be interpreted as known auth method(s). |
| 50131 | Device is not in required device state: {state}. Or, the request was blocked due to suspicious activity, access policy, or security policy decisions. |
| 50132 | The session is not valid due the following reasons: password expiration or recent password change, SSO Artifact is invalid or expired, session is not fresh enough for application, or a silent sign-in request was sent but the user’s session with Azure AD is invalid or has expired. |
| 50133 | The session is not valid due to password expiration or recent password change. |
| 50134 | Wrong data center. To authorize a request that was initiated by an app in the OAuth 2.0 device flow, the authorizing party must be in the same data center where the original request resides. |
| 50135 | Password change is required due to account risk. |
| 50136 | Single MSA session detected when requesting an MSA ticket. |
| 50137 | Password needs to be changed due to security policy rule. |
| 50138 | Invalid encryption key environment. |
| 50139 | Session is invalid due to missing an external refresh token. |
| 50140 | This occurred due to ‘Keep me signed in’ interrupt when the user was signing in. |
| 50141 | Protected key is not intended for the authenticated user. |
| 50142 | Password change is required due to a conditional access policy. |
| 50143 | Session mismatch. The session is invalid because user tenant does not match the domain hint. |
| 50144 | The user’s Active Directory password has expired. |
| 50146 | This application is required to be configured with an application-specific signing key. It is either not configured with one, or the key has expired or is not yet valid. |
| 50147 | Invalid size of the code challenge parameter. |
| 50148 | The code_verifier does not match the code_challenge supplied in the authorization request for PKCE. |
| 50149 | Invalid Code_Challenge_method parameter. |
| 50150 | The provided credentials does not have a valid user consent approval information. |
| 50155 | Device authentication failed. |
| 50156 | Device tokens are not supported for V2 resource. |
| 50157 | User redirection required for routing. |
| 50158 | External security challenge not satisfied. User will be redirected to another page or authentication provider to satisfy additional authentication challenges. |
| 50159 | Claims sent by external provider are not enough. |
| 50160 | Different target tenant is preferred. |
| 50161 | Failed to validate authorization url of external claims provider. |
| 50168 | The client is capable of utilizing the Windows 10 Accounts extension to perform SSO but no SSO token was found in the request or the token was expired. Request has been interrupted to attempt to pull an SSO token. |
| 50169 | The realm ‘{realm}’ is not a configured realm of the current service namespace. |
| 50170 | The external controls mapping is missing. |
| 50172 | External claims provider {provider} is not approved. |
| 50173 | The provided grant has expired due to it being revoked, a fresh auth token is needed. The user might have changed or reset their password. The grant was issued on ‘{authTime}’ and the TokensValidFrom date (before which tokens are not valid) for this user is ‘{validDate}’. |
| 50176 | Missing definition of external control: {controlId}. |
| 50177 | User account ‘{user}’ from identity provider ‘{idp}’ does not exist in tenant ‘{tenant}’ and cannot access the application ‘{appId}’({appName}) in that tenant. The account needs to be added as an external user in the tenant first. Sign out and sign in again with a different Azure Active Directory user account. |
| 50178 | User account ‘{user}’ from identity provider ‘{idp}’ does not exist in tenant ‘{tenant}’ and cannot access the application ‘{appId}’({appName}) in that tenant. The account needs to be added as an external user in the tenant first. Sign out and sign in again with a different Azure Active Directory user account. |
| 50179 | Client_info is not supported for this user. |
| 50180 | Integrated Windows Authentication is needed. Enable the tenant ‘{name}’ for Seamless SSO. |
| 50181 | Unable to validate the otp. |
| 50182 | OTP is already expired. |
| 50183 | Cannot lookup otp due to cache error. |
| 50184 | OTP is incorrect, or no cache entry exists for the tenant/user. |
| 50185 | Email OTP notification delivery failed. |
| 50186 | Unpermitted realm. |
| 50187 | Failed to perform device authentication. |
| 50189 | The device code is not correctly formatted. |
| 50190 | Region prefix to connection string mapping returned from settings is null. |
| 50192 | Invalid request. |
| 50193 | Internal use |
| 50194 | Application ‘{appId}’({appName}) is not configured as a multi-tenant application. Usage of the /common endpoint is not supported for such applications created after ‘{time}’. Use a tenant-specific endpoint or configure the application to be multi-tenant. |
| 50196 | The server terminated an operation because it encountered a client request loop. Please contact your app vendor. |
| 50197 | Sorry, we could not find the user, please sign-in again. |
| 50199 | For security reasons, user confirmation is required for this request. Please repeat the request allowing user interaction. |
| 50200 | Unpermitted external trusted realm. |
| 50201 | This message prompt interrupt will be shown to the user during login when additional information should be provided to user. |
| 50202 | User is not registered in the organization and must explicitly consent to the sign-in. |
| 50203 | User has not registered the authenticator app and must register or snooze this notification. |
| 50204 | External user has not consented to the privacy statement. |
| 50205 | External user has consented to the privacy statement. |
| 50206 | The user or administrator has not consented connecting to the target-device: ‘{identifier}’. Send an interactive authorization request for this user and target-machine. |
| 50207 | This web native bridge interrupt will be shown to the user during login when the application is requesting login through the native broker and needs eSTS to ensure the broker is properly configured. |
| 50208 | This web native bridge interrupt was shown, but the native bridge unexpectedly returned a different user. |
| 50209 | User is performing a password reset. |
| 53000 | Device is not in required device state: {state}. Conditional Access policy requires a compliant device, and the device is not compliant. The user must enroll their device with an approved MDM provider like Intune. |
| 53001 | Device is not in required device state: {state}. Conditional Access policy requires a domain joined device, and the device is not domain joined. |
| 53002 | Device is not in required device state: {state}. The app used is not an approved app for Conditional Access. |
| 53003 | Access has been blocked by Conditional Access policies. The access policy does not allow token issuance. |
| 53004 | Cannot configure multi-factor authentication methods due to suspicious activity. |
| 53005 | Application needs to enforce Intune protection policies. |
| 53006 | Authentication required from federated idP. |
| 53007 | Authentication required from federated IDP. |
| 53008 | Browser not supported. |
| 53009 | Application needs to enforce Intune protection policies. |
| 53010 | Cannot configure multi-factor authentication methods because the organization requires this information to be set from specific locations or devices. |
| 53011 | User blocked due to risk on home tenant. |
| 54000 | User is not allowed to access application {appName} due to Legal Age Group Requirement of application {audience}. |
| 54005 | OAuth2 Authorization code was already redeemed, please retry with a new valid code or use an existing refresh token. |
| 54006 | Unencrypted v2 access tokens are not supported for first party applications that support consumer accounts. The resource must add a certificate to the onboarding portal to encrypt tokens. |
| 54007 | Method not supported for IDP OAuth2 Federation. |
| 54008 | Multi-Factor authentication is required and the credential used ({credentialName}) is not supported as a First Factor. Contact your administrator for more information. |
| 54009 | Multi-Factor authentication is required and the credential used is not supported. Contact your administrator for more information. |
| 54010 | Proofup blocked due to credential used not supported. Contact your administrator for more information. |
| 65001 | The user or administrator has not consented to use the application with ID ‘{identifier}’{namePhrase}. Send an interactive authorization request for this user and resource. |
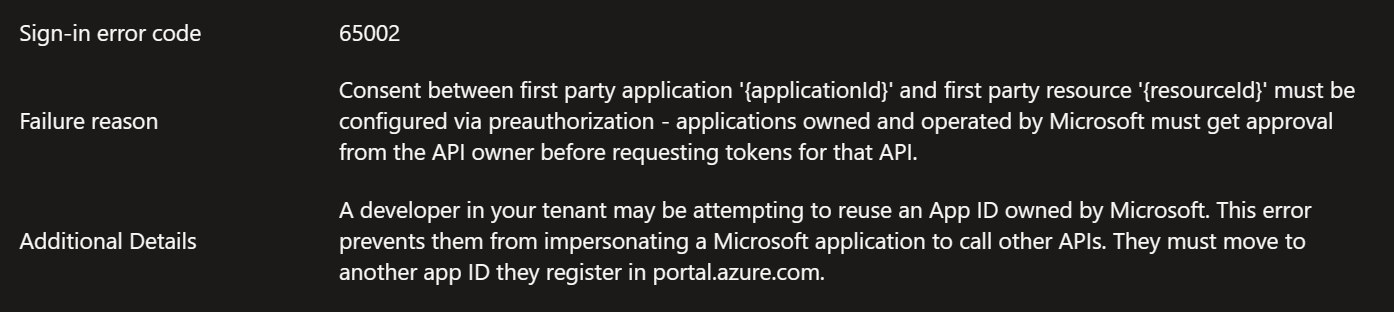
| 65002 | Consent between first party application ‘{applicationId}’ and first party resource ‘{resourceId}’ must be configured via preauthorization - applications owned and operated by Microsoft must get approval from the API owner before requesting tokens for that API. |
| 65003 | Consent for first party token-to-self must be configured via preauthorization. If preauthorization has already been configured, update the request to use a URI identifier for the resource instead of ‘{resourceId}’ to work around this error. |
| 65004 | User declined to consent to access the app. |
| 65005 | The application ‘{name}’ asked for scope ‘{scope}’ that doesn’t exist. |
| 65006 | Resource ‘{resourceId}’ had no entitlements matching required permissions configured on the required resource access for client ‘{clientId}’. Requested permission IDs: ‘{permissionId}’. This is a problem with one or more invalid permission ids on the client RRA configuration or the resource entitlement configuration. |
| 65007 | Client ‘{clientId}’ required resource access configuration has changed and therefore the request could not be completed. Please try again. |
| 70024 | OIDC Provider Metadata missing required field ‘{fieldName}’. |
| 70030 | Remote authentication failed to read session from storage. |
| 70031 | Remote authentication session is in a bad state. |
| 70033 | The remote auth session with this device code has already been approved. |
| 70034 | The remote auth session with this device code has already been denied. |
| 70035 | Remote auth session with this device code doesn’t exist. |
| 70036 | Unsupported remote auth session state. |
| 70037 | Incorrect challenge response provided. Remote auth session denied. |
| 70039 | The remote auth session with this device code has expired. |
| 70041 | Unable to complete OAuth2 IdP’s sign in. The ’nonce’ claim does not match the expected value. |
| 70043 | The refresh token has expired or is invalid due to sign-in frequency checks by conditional access. The token was issued on {issueDate} and the maximum allowed lifetime for this request is {time}. |
| 70044 | The session has expired or is invalid due to sign-in frequency checks by conditional access. |
| 70045 | The refresh token is invalid due to sign-in frequency checks by conditional access. Additionally, since the sign-in frequency policy applies to all applications, the token will never be usable, and should be deleted. The authInstant in this token was {authInstant} and the maximum allowed lifetime for this request is {time}. |
| 70046 | The session has expired or is invalid due to re-authentication checks by conditional access. |
| 81001 | Service ticket size exceeded the maximum allowed. |
| 81004 | Kerberos authentication failed. |
| 81005 | Authentication package is not supported. |
| 81006 | No authorization header was found, returning 401 WWW-Authenticate. |
| 81007 | Tenant is not enabled for DesktopSSO. |
| 81008 | Failed to validate Kerberos ticket. |
| 81009 | Unable to validate the user’s Kerberos ticket, the authorization header value is not formatted correctly. |
| 81010 | Seamless SSO failed because the user’s Kerberos ticket has expired or is invalid. |
| 81011 | Failed to find user by on-premise SID in the user’s Kerberos ticket. |
| 81012 | The user trying to sign in to Azure AD is different from the user signed into the device. |
| 81013 | Failed to lookup the user whose kerberos ticket was used to login. |
| 81014 | The DesktopSSO auth token has expired. |
| 81015 | Rejecting DesktopSSO Kerberos ticket as it was obtained through delegation. Delegated Kerberos ticket does not originate from user directly. Please contact your tenant administrator to disable delegation on the AZUREADSSOACC account. |
| 81016 | Invalid STS request. |
| 90000 | Internal use |
| 90002 | Tenant ‘{tenant_name}’ not found. Check to make sure you have the correct tenant ID and are signing into the correct cloud. Check with your subscription administrator, this may happen if there are no active subscriptions for the tenant. |
| 90004 | The request is not properly formatted. |
| 90005 | Unable to complete request. The request was invalid since SID and login_hint cannot be used together. |
| 90006 | A transient error has occurred. Please try again. |
| 90007 | Bad Request. The passed session ID cannot be parsed. |
| 90008 | The user or administrator has not consented to use the application with ID ‘{appId}’({appName}). This happened because application is misconfigured: it must require access to Microsoft Graph by specifying at least ‘Sign in and read user profile’ permission. |
| 90009 | Application ‘{appId}’({appName}) is requesting a token for itself. This scenario is supported only if resource is specified using the GUID based App Identifier. |
| 90010 | Unable to create {algoName} algorithm. |
| 90012 | This request has timed out. |
| 90013 | Invalid input received from the user. |
| 90014 | The required field ‘{name}’ is missing from the credential. Ensure that you have all the necessary parameters for the login request. |
| 90015 | Requested query string is too long. |
| 90016 | Invalid access token. Required claim is missing. |
| 90017 | Unexpected field ‘{fieldName}’. |
| 90019 | No tenant-identifying information found in either the request or implied by any provided credentials. |
| 90020 | The SAML 1.1 Assertion is missing ImmutableID of the user. |
| 90022 | Principal name format is invalid for ‘{name}’. Expected format: name[/instance][@realm]. The principal name is required, host and realm are optional and may be set to null. |
| 90023 | Invalid STS request. |
| 90024 | A transient error has occurred. Please try again. |
| 90025 | Request processing has exceeded internal allowance. This operation will be retried internally and usually resolves without user impact. Please verify the end result of the transaction to verify status. |
| 90026 | Hostname contains an invalid wildcard ‘*’ character. |
| 90027 | We are unable to issue tokens from this API version on the MSA tenant. Please contact the application vendor as they need to use version 2.0 of the protocol to support this. |
| 90028 | Principal name format is invalid for name ‘{name}’. Primary component of the name is required. |
| 90029 | The realm ‘{name}’ is a Unicode domain name. Domain names of this form are not supported. |
| 90030 | A transient error has occurred. Try again after some time. |
| 90031 | A transient error has occurred. Try again after some time. |
| 90032 | A transient error has occurred. Try again after some time. |
| 90033 | A transient error has occurred. Please try again. |
| 90035 | Service is temporarily unavailable. Please retry later. |
| 90036 | An unexpected, non-retryable error stemming from the directory service has occurred. |
| 90037 | Non-retryable error has occurred. |
| 90038 | Tenant ‘{tenant_name}’ request is being redirected to the National Cloud ‘{cloud}’. |
| 90039 | Service is temporarily unavailable. Please retry later. |
| 90040 | A non-retryable error has occurred. |
| 90041 | A transient error has occurred. Please try again. |
| 90042 | National Cloud Name is missing in the postback request. |
| 90043 | OAuth2 grant was issued by National Cloud STS. |
| 90044 | National Cloud Request Process Switched off. |
| 90045 | Service is too busy. Please try again later. |
| 90046 | Internal use |
| 90047 | Internal use |
| 90049 | Application could not be found. |
| 90050 | Response content length from external IdP exceeds supported limit. |
| 90051 | Invalid Delegation Token. Invalid national Cloud ID ({cloudId}) is specified. |
| 90052 | Actual message content is runtime specific. Please see returned exception message for details. |
| 90072 | User account ‘{user}’ from identity provider ‘{idp}’ does not exist in tenant ‘{tenant}’ and cannot access the application ‘{application}’({appName}) in that tenant. The account needs to be added as an external user in the tenant first. Sign out and sign in again with a different Azure Active Directory user account |
| 90073 | Invalid Fairfax Gateway Redirect. |
| 90081 | An error occurred when the service tried to process a WS-Federation message. The message was invalid, malformatted, or contains potentially dangerous characters. |
| 90082 | Authentication policy ‘{name}’ selected for the request is not currently supported. |
| 90083 | Request is unsupported. |
| 90084 | Guest accounts are not allowed for this site. |
| 90085 | The service is unable to issue a token because the company object hasn’t been provisioned yet. |
| 90086 | The user DA token is expired. |
| 90087 | An error occurred while creating the WS-Federation message from the URI. |
| 90088 | Authentication failed due to email address domain is not in allowed domains list for identity provider. |
| 90089 | User token should not be used in App on behalf of flow. |
| 90090 | A transient error has occurred. Please try again. |
| 90091 | A transient error has occurred. Please try again. |
| 90092 | Non-retryable error has occurred. |
| 90093 | Actual message content is runtime specific. Please see returned exception message for details. |
| 90094 | Admin consent is required for the permissions requested by this application. |
| 90095 | Admin consent is required for the permissions requested by this application. An admin consent request may be sent to the admin. |
| 90096 | Admin consent is required for the permissions requested by this application. Admin consent request sent for processing. |
| 90097 | An error has occured during admin consent processing. |
| 90098 | An unexpected approval request ID was provided. |
| 90099 | The application ‘{appId}’ ({appName}) has not been authorized in the tenant ‘{tenant}’. Applications must be authorized to access the customer tenant before partner delegated administrators can use them. |
| 90100 | {name} parameter is empty or not valid. |
| 90101 | The supplied data isn’t a valid email address. Please provide it in the format someone@example.com |
| 90102 | ‘{name}’ value must be a valid absolute URI. |
| 90107 | The request is not valid. Make sure your data doesn’t have invalid characters. |
| 90112 | Application identifier is expected to be a GUID. |
| 90114 | The specified bulk AADJ token expiration timestamp will cause an expired token to be issued. |
| 90116 | {method} request is made, while POST is the only supported verb. |
| 90117 | Invalid request. |
| 90119 | The user code is null or missing. |
| 90120 | This request was already authorized or declined. |
| 90121 | Invalid empty request. |
| 90122 | User identifier is not present. |
| 90123 | The token can’t be issued because the identity or claim issuance provider denied the request. Response code: {errorCode}. |
| 90124 | {resConstant} ‘{resourceId}’ {resourceName} is not supported over the /common or /consumers endpoints. Please use the /organizations or tenant-specific endpoint. |
| 90125 | {userName} isn’t in our system. Make sure you entered the user name correctly. |
| 90126 | User Type is not supported on this endpoint. The system can’t infer the user’s tenant from the user name: {userName} |
| 90128 | Unable to load OptIn store for user. |
| 90129 | {resConstant} ‘{resourceId}’ {resourceName} has a configured token version of ‘1’ and is not supported over the /common or /consumers endpoints. |
| 90130 | {appConstant} ‘{appId}’ {appName} is not supported over the /common or /consumers endpoints. Please use the /organizations or tenant-specific endpoint. |
| 90131 | Invalid ambiguous request. sid cannot be used with prompt {prompt}. |
| 90132 | The provided value for the input parameter ‘device_code’ is not valid. Device codes supporting the personal Microsoft Account sign-in audience can only be used for v2 common or consumers tenants. |
| 90134 | Retrieving claims from identity provider ‘{idp}’ failed. |
| 90135 | The user decided not to continue the authentication. No remediation is required. |
| 90136 | Device Code flow is not supported for Confidential Clients. |
| 90137 | Token issuance cannot proceed because user declined consent approval to release their profile information. |
| 90138 | Invalid ambiguous request. sid cannot be used with login_hint. |
| 90139 | Invalid request. The device code flow connect mode in your request is only supported for the /consumers/ tenant. |
| 90150 | Failed to read request. |
| 130001 | Signature key ID is not provided. |
| 130004 | UserPrincipal doesn’t have the NGC key configured. |
| 130005 | NGC key signature verification failed. |
| 130006 | The NGC transport key isn’t configured on the device. |
| 130007 | The device is disabled. |
| 130008 | Device referenced by the NGC key is not found. |
| 130009 | Device key was found weak. |
| 130500 | Phone sign in was blocked due to User Credential Policy. |
| 130501 | Sign in was blocked due to User Credential Policy. |
| 130502 | Temporary Access Pass sign in was blocked due to User Credential Policy. |
| 130503 | Your Temporary Access Pass is incorrect. If you don’t know your pass, contact your administrator. |
| 130504 | Your Temporary Access Pass has expired. Contact your administrator to obtain a new pass. |
| 130505 | Your one-time Temporary Access Pass has been redeemed. Contact your admin to get a new pass. |
| 130506 | Access Pass must be used for Web Sign In. Contact your admin to get an Access Pass. |
| 130507 | An access pass could not be found or verified for the user. |
| 135000 | Fido signature verification failed. |
| 135001 | UserPrincipal doesn’t have the key ID configured. |
| 135002 | Fido key does not have authenticator data. |
| 135003 | Fido assertion verification failed. Invalid gesture provided. |
| 135004 | Invalid postBackUrl parameter. |
| 135005 | Invalid cancelUrl parameter. |
| 135006 | Invalid resumeUrl parameter. |
| 135007 | Client data type is not valid. |
| 135008 | Relying Party Origin is not valid. |
| 135009 | Flow Token Scenario must be login scenario. |
| 135010 | UserPrincipal doesn’t have the key ID configured. |
| 135011 | Device used during the authentication is disabled. |
| 135012 | UserObjectId from the UserHandle does not match with UserPrincipal UserObjectId. |
| 135013 | Invalid UserHandle prefix. |
| 135014 | Invalid UserHandle length. |
| 135015 | The FIDO exclude list was not a valid JSON blob. |
| 135016 | FIDO sign-in is disabled via policy. |
| 135017 | Unexpected Signature Counter received from authenticator. |
| 135018 | Invalid challenge received from fido assertion. |
| 135019 | Expired Challenge received from Fido assertion. |
| 135020 | Invalid Fido assertion. |
| 135021 | Invalid UserHandle prefix. |
| 135022 | Redirect uri provided by MSA is not valid. |
| 140000 | Request nonce is expired. Current time: {curTime}, expiry time of assertion {expTime}. |
| 140001 | The session key is not valid. |
| 140002 | Key not found |
| 140003 | Nonce purpose not supported |
| 140004 | Invalid Ticket Granting Ticket request. |
| 140005 | Invalid Ticket Granting Ticket request. |
| 140006 | Invalid Ticket Granting Ticket request. |
| 140007 | Invalid Ticket Granting Service request. |
| 140008 | Invalid ApReq assertion provided. |
| 140009 | Kerberos crypto bad request |
| 140010 | Kerberos ticket validation failure |
| 160011 | Selected user account was invalid. |
| 160021 | Application requested a user session which does not exist. |
| 240000 | Limit for BulkAADJ tokens is reached for the tenant. |
| 240001 | User is not authorized to register devices in Azure AD. |
| 240002 | Input id_token cannot be used as ‘urn:ietf:params:oauth:grant-type:jwt-bearer’ grant. |
| 240003 | Unexpected result from authorize endpoint call. |
| 240004 | Authorization code not received from authorize endpoint call. Error: {errorInfo} |
| 240005 | Missing required user role to acquire a bulk AADJ token. For more information please go to https://go.microsoft.com/fwlink/?linkid=2224591. |
| 399206 | An unexpeted and non-retryable error happened when fetching bloomfilter data from blob storage. |
| 399207 | The token request does not contain one or more supported response token type(s): ‘{ResType}’. |
| 399208 | Registered certificates must not be used for token binding for public clients. Please use ephemeral client certificates. |
| 399209 | Application ‘{appIdentifier}’ does not have certificate-bound access tokens enabled. |
| 399210 | A verifiable credential is required to access this resource. |
| 399211 | Unable to find the requested DiskCache. |
| 399212 | Requested DiskCache is expired. |
| 399213 | The device key supplied is invalid. |
| 399214 | The algorithm in the request is invalid. |
| 399215 | HttpRequestException occurred in request to Dsts. |
| 399216 | Timeout occurred in request to Dsts. |
| 399217 | Non-retryable error has occurred. |
| 399218 | For security reasons, user confirmation is required for this request. Please repeat the request allowing user interaction. |
| 399219 | MSA Data Accessor transient timeout. |
| 399220 | More than one service principal returned |
| 399229 | Multiple MAM Browser client IDs are present in the claims collection. Values: {values} |
| 399230 | MAM Browser application principal ‘{appPrincipalId}’ is not valid in the directory |
| 399231 | MAM Browser application principal ‘{appPrincipalId}’ does not have any usable reply address in the directory |
| 399232 | MAM Browser application principal ‘{appPrincipalId}’ reply address validation failed. Reason: ‘{reason}’ |
| 399233 | DstsCache is missing the Signingkey info |
| 399234 | Recieved public Signingkey response has XML parsing error |
| 399235 | Invalid Soap Headers passed to Dsts request |
| 399236 | Invalid Soap Body passed to Dsts request |
| 399237 | Failure when proxying a request from DstsCache to legacy dSTS |
| 500011 | The resource principal named {name} was not found in the tenant named {tenant}. This can happen if the application has not been installed by the administrator of the tenant or consented to by any user in the tenant. You might have sent your authentication request to the wrong tenant. |
| 500012 | Resource application name ‘{name}’ is not valid. |
| 500013 | Resource identifier is not provided. |
| 500014 | The service principal for resource ‘{identifier}’ is disabled. This indicate that a subscription within the tenant has lapsed, or that the administrator for this tenant has disabled the application, preventing tokens from being issued for it. |
| 500015 | MSA provisioned resources are not supported in the tenant named {tenant}. |
| 500016 | Application ‘{appIdentifier}’ is not supported as a resource application to execute the flow. |
| 500017 | Application ‘{appIdentifier}’ is not allowed as a resource application to execute the flow. |
| 500021 | Access to ‘{tenant}’ tenant is denied. |
| 500022 | Access to ‘{tenant}’ tenant is denied. |
| 500023 | ‘{headerFromCredential}’ is not the same as ‘{headerFromRequest}’. |
| 500024 | Conflicting tenant restrictions signals received by the server on the login request. The header indicated ‘{headerFromRequest}’ while the application added a claims request for ‘{headerFromClaims}’. This can indicate conflicting network and device policies, which Azure AD does not support. |
| 500025 | Conflicting tenant restrictions signals received by the server from a claims request. The header from the Id Token ‘{headerFromIdToken}’ is different than the header from the access token ‘{headerFromAccessToken}’. |
| 500031 | Cannot find signing certificate configured. |
| 500032 | Cannot find signing certificate/private key to issue a certificate. |
| 500033 | There is an issue with the key ‘{kid}’. It has both x5t and x5c values, but they do not match. Please make sure the x5t value is the Base64Url-encoded SHA-1 thumbprint of the first certificate in x5c. |
| 500081 | SAML assertion validation failed: no supported token signature is provided. |
| 500082 | SAML assertion is not present in the token. |
| 500083 | Unable to verify token signature. No trusted realm was found with identifier ‘{issuer}’. |
| 500084 | Cannot read SecurityToken. Expected element is ({expectedName}, {expectedNamespace}) the actual element is ({localName}, {actualNamespace}). |
| 500085 | SAML Assertion with MajorVersion ‘{actualMajor}’ and MinorVersion ‘{actualMinor}’ is not supported. The supported version is MajorVersion ‘{major}’ and MinorVersion ‘{minor}’. |
| 500086 | SAML Assertion AssertionId ‘{id}’ is not a valid xsd:ID value. |
| 500087 | SAML Assertion does not have any SAML Statement elements. SAML Assertion must have at least one SAML Statement element. |
| 500088 | SAML Assertion is missing the required ‘{name}’ Attribute. |
| 500089 | SAML 2.0 assertion validation failed: {details} |
| 500101 | Audience URI validation failed. No token audiences were found. |
| 500102 | Audience URI validation failed. No allowed audiences are configured. |
| 500103 | Validation of Audience URI(s) {uri} failed. No match was found with allowed audience(s) {audience}. |
| 500111 | The reply uri specified in the request has an invalid scheme. |
| 500112 | The reply address ‘{actual}’ does not match the reply address ‘{provided}’ provided when requesting Authorization code. |
| 500113 | No reply address is registered for the application{idPhrase}. |
| 500114 | Protocol not specified for reply address validation. |
| 500115 | The reply uri specified in the request is missing or not a valid URL. |
| 500116 | The reply uri specified in the request is not a valid URL. Allowed schemes: ‘{schemes}’. |
| 500117 | The reply uri specified in the request isn’t using a secure scheme. |
| 500118 | The reply uri specified in the request failed validation. The reply uri host must match one of the registered DNS host names ‘{host}’ for site with ID ‘{id}’. |
| 500119 | Redirect URIs with urn: schemes are prohibited. Use a different scheme, or https://login.microsoftonline.com/common/oauth2/nativeclient |
| 500121 | Authentication failed during strong authentication request. |
| 500122 | SWT assertion failed signature validation. Actual message content is runtime specific. Please see returned exception message for details. |
| 500123 | SWT assertion failed signature validation. Actual message content is runtime specific. Please see returned exception message for details. |
| 500124 | No device secret is provisioned in the store. |
| 500125 | Invalid device secret is provided. |
| 500126 | External ID token from issuer ‘{issuer}’ failed signature verification. KeyID of token is ‘{identifier}’. |
| 500127 | No authenticated credentials found in request. |
| 500128 | No session key found. |
| 500129 | No NGC transport key found. |
| 500131 | Assertion audience does not match the Client app presenting the assertion. The audience in the assertion was ‘{tokenAudience}’ and the expected audience is ‘{expectedAudience}’ or one of the Application Uris of this application with App ID ‘{appId}’({appName}). The downstream client must request a token for the expected audience (the application that made the OBO request) and this application should use that token as the assertion. |
| 500132 | Assertion is malformed and cannot be read. |
| 500133 | Assertion is not within its valid time range. Ensure that the access token is not expired before using it for user assertion, or request a new token. Current time: {curTime}, expiry time of assertion {expTime}. |
| 500135 | Authentication code is missing in the assertion. |
| 500136 | The token issuer doesn’t match the api version: A version 2 token can only be used with the v2 endpoint. |
| 500137 | The token issuer doesn’t match the api version: A version 1 token cannot be used with the v2 endpoint. |
| 500138 | No Refresh Token claim provided in the assertion. |
| 500139 | Refresh token in the assertion is not a primary refresh token. |
| 500141 | The user’s redemption is complete but the request was not initiated by the target application. |
| 500142 | The user’s redemption is complete and the sign-in should continue. |
| 500183 | Certificate has been revoked. |
| 500184 | Client assertion JWT token failed verification during certificate based authentication. The token is not signed by the certificate provided in the token. |
| 500185 | Tenant differs between user login and certificate user. |
| 500186 | User not allowed by policy conditions. |
| 500187 | Selected certificate does not meet the criteria. |
| 500200 | User account ‘{email}’ is a personal Microsoft account. Personal Microsoft accounts are not supported for this application unless explicitly invited to an organization. Try signing out and signing back in with an organizational account. |
| 500201 | We are unable to issue tokens from this API version for a Microsoft account. Please contact the application vendor as they need to use version 2.0 of the protocol to support this. |
| 500202 | User account ‘{email}’ from external identity provider ‘{idp}’ is not supported for API version ‘{version}’. Microsoft account pass-thru users and guests are not supported by the tenant-independent endpoint. |
| 500204 | Microsoft account ‘{email}’ can’t be used to log in to application {appName}. Please get this user invited to {tenant} directory or sign out and sign in again with a Work or School account. |
| 500205 | A consumer (B2C) account can’t be used to log into non consumer applications. |
| 500206 | The account type can’t be used for the application you’re trying to log into. |
| 500207 | The account type can’t be used for the resource you’re trying to access. |
| 500208 | The domain is not a valid login domain for the account type. |
| 500209 | Unspecific Tenant is not supported in this domain. |
| 500210 | Domain name does not match with the tenant identifier |
| 500211 | User account ‘{email}’ from identity provider ‘{idp}’ does not exist in tenant ‘{tenant}’ and cannot access the application ‘{appId}’({appName}) in that tenant. The account needs to be added as an external user in the tenant first. Sign out and sign in again with a different Azure Active Directory user account. |
| 500212 | The user’s administrator has set an outbound access policy that does not allow access to the resource tenant. |
| 500213 | The resource tenant’s cross-tenant access policy does not allow this user to access this tenant. |
| 500331 | An error occurred while attempting to create a certificate from bytes. |
| 500341 | The user account {identifier} has been deleted from the {tenant} directory. To sign into this application, the account must be added to the directory. |
| 500342 | User account is not configured for remote NGC. |
| 500343 | Could not create remote sign-in session. |
| 500344 | User Account is not found for Fido Sign in flow. |
| 500346 | E-Mail OTP user cannot sign in with local password. |
| 500571 | The guest user account is disabled. |
| 500581 | Rendering JavaScript. Fetching sessions for single-sign-on on V2 with prompt=none requires javascript to verify if any MSA accounts are signed in. |
| 500582 | Microsoft Account session_id with prompt=none not supported on AAD tenant. |
| 500583 | Storage Access required. |
| 500881 | Limit on telecom MFA calls reached. Please retry with PhoneAppNotification or try again in a few minutes. |
| 500882 | Limit on telecom MFA calls reached. Please retry with PhoneAppCode or try again in a few minutes. |
| 500883 | Limit on telecom MFA calls reached. Please retry with CompanionAppsNotification or try again in a few minutes. |
| 501271 | Broker app needs to be installed for device authentication to succeed. |
| 501291 | Client app is a Mam app, device is not registered and request is sent using a broker. Work place join needs to be done to register the device before the app can be accessed. |
| 501292 | Client application cannot satisfy app protection requirement. If it’s a first party app, then it’s not whitelisted to be used with app protection policies, otherwise, the app has not advertised as app-compliant capable, or the authentication library used does not support app protection policies. |
| 501293 | The device is not workplace joined. To proceed with the ‘Sign in from another device’ option, this device must be workplace joined. |
| 501311 | Browser not supported. |
| 501312 | Device used during the authentication is not registered for the account. |
| 501313 | Your device is required to be managed to access this resource. |
| 501314 | Silent interrupt required to recognize browser capabilities. Used to differentiate between Safari running in iPadOS or Mac. |
| 501471 | Missing code_challenge parameter. |
| 501481 | The Code_Verifier does not match the code_challenge supplied in the authorization request. |
| 501482 | The Code_Verifier length is less than invalid. |
| 501491 | Invalid size of Code_Challenge parameter. |
| 501811 | OTP is incorrect, or no cache entry exists for the tenant/user. |
| 530001 | Browser not supported. |
| 530002 | Your device is required to be compliant to access this resource. |
| 530003 | Your device is required to be managed to access this resource. |
| 530004 | AcceptCompliantDevice setting isn’t configured for this organization. The admin needs to configure this setting to allow external users access to protected resources. |
| 530011 | Browser not supported. |
| 530021 | Application does not meet the conditional access approved app requirements. |
| 530022 | Browser not supported. |
| 530031 | Access policy does not allow token issuance. |
| 530032 | User blocked due to risk on home tenant. |
| 530033 | Remote device flow blocked due to device based conditional access. |
| 530034 | A delegated administrator was blocked from accessing the tenant due to account risk. |
| 530035 | Access has been blocked by security defaults. |
| 650041 | User terminated the request. |
| 650051 | Actual message content is runtime specific. Please see returned exception message for details. |
| 650052 | The app is trying to access a service ‘{appId}’({appName}) that your organization ‘{organization}’ lacks a service principal for. Contact your IT Admin to review the configuration of your service subscriptions or consent to the application in order to create the required service principal. |
| 650053 | The application ‘{name}’ asked for scope ‘{scope}’ that doesn’t exist on the resource ‘{resource}’. Contact the app vendor. |
| 650054 | The application ‘{name}’ asked for permissions to access a resource that has been removed or is no longer available. Contact the app vendor. |
| 650055 | The application ‘{name}’ required resource access list does not contain applications discoverable by ‘{resource}’. |
| 650056 | Misconfigured application. This could be due to one of the following: the client has not listed any permissions for ‘{name}’ in the requested permissions in the client’s application registration. Or, the admin has not consented in the tenant. Or, check the application identifier in the request to ensure it matches the configured client application identifier. Or, check the certificate in the request to ensure it’s valid. Please contact your admin to fix the configuration or consent on behalf of the tenant. Client app ID: {id}. |
| 650057 | Invalid resource. The client has requested access to a resource which is not listed in the requested permissions in the client’s application registration. Client app ID: {appId}({appName}). Resource value from request: {resource}. Resource app ID: {resourceAppId}. List of valid resources from app registration: {regList}. |
| 650058 | The app needs access to a service that your organization has not subscribed to or enabled. Contact your IT Admin to review the configuration of your service subscriptions. |
| 650061 | The client application {appDisplayName} ({applicationId}) requested the role {roleName} ({roleId}) on the resource application {resourceDisplayName} ({resourceId}) but this role is only assignable to users. Either the client application vendor must remove the role from the requested roles, or the owner of the resource application must allow the role to be assignable to applications. For more information, see https://docs.microsoft.com/azure/active-directory/develop/howto-add-app-roles-in-azure-ad-apps |
| 700001 | Application: {samlAudience} needs to opt-in for ‘aio’ optional claim for On Behalf Of flow to work with SAML tokens issued to this application |
| 700002 | SAML 1.1 Bearer assertion must be a valid Base64 encoded value. |
| 700003 | Device object was not found in the tenant ‘{tenantName}’ directory. |
| 700004 | onpremobjectguid ‘{objGuid}’ attribute in the presented grant is malformed. |
| 700005 | Provided Authorization Code is intended to use against other tenant, thus rejected. |
| 700006 | The Audience: {audience} of the token is NOT an absolute Uri |
| 700007 | The grant was issued for a different client id. |
| 700008 | Social IDP users are not expected to have home tenant. |
| 700009 | Reply address must be provided when presenting an authorization code requested with an explicit reply address. |
| 700011 | Application with identifier {appIdentifier} was not found in the directory. |
| 700012 | Missing Authorization header with bearer token. Client was not authenticated. |
| 700013 | Client is not authorized to request managed browser purpose token. |
| 700014 | Mobile Edge app needs to provide an enrollment id in order to acquire a purpose token that can satisfy the compliant app requirement. |
| 700016 | Application with identifier ‘{appIdentifier}’ was not found in the directory ‘{tenantName}’. This can happen if the application has not been installed by the administrator of the tenant or consented to by any user in the tenant. You may have sent your authentication request to the wrong tenant. |
| 700017 | {resourceConstant} ‘{resourceIdentifier}’ is not supported as resource. |
| 700018 | {resourceConstant} ‘{resourceIdentifier}’ is not supported as resource. |
| 700019 | Application ID {identifier} cannot be used or is not authorized. |
| 700020 | Application ID {identifier} is a reserved identifier and should be removed on the application: {applicationId}. |
| 700021 | Client assertion application identifier doesn’t match ‘client_id’ parameter. Review the documentation at https://docs.microsoft.com/azure/active-directory/develop/active-directory-certificate-credentials . |
| 700022 | No Subject claim provided in the assertion. Review the documentation at https://docs.microsoft.com/azure/active-directory/develop/active-directory-certificate-credentials . |
| 700023 | Client assertion audience claim does not match Realm issuer. Review the documentation at https://docs.microsoft.com/azure/active-directory/develop/active-directory-certificate-credentials . |
| 700024 | Client assertion is not within its valid time range. Current time: {curTime}, assertion valid from {validTime}, expiry time of assertion {expTime}. Review the documentation at https://docs.microsoft.com/azure/active-directory/develop/active-directory-certificate-credentials . |
| 700025 | Client is public so neither ‘client_assertion’ nor ‘client_secret’ should be presented. |
| 700026 | Client application has no configured keys. |
| 700027 | Client assertion failed signature validation. |
| 700028 | Certificate with thumbprint {thumbprint} is not authorized. |
| 700029 | Invalid signing certificate. |
| 700030 | Invalid certificate - subject name in certificate is not authorized. SubjectNames/SubjectAlternativeNames (up to 10) in token certificate are: {certificateSubjects}. |
| 700031 | Invalid certificate - SubjectName or SubjectAlternativeName is missing |
| 700032 | Invalid certificate - Trusted Certificate Subjects for application are missing |
| 700033 | For asserting custom_claims, client must provide either xms_actor_token or subject name issuer certificate with custom claim allowed values. |
| 700034 | Client assertion contains an invalid xms_actor_token claim. |
| 700035 | Client assertion contains custom_claims in the incorrect format. |
| 700036 | Client is not authorized to override managed identity claim in the token. |
| 700037 | Client assertion must declare x5c header when overriding managed resource ID. |
| 700038 | 00000000-0000-0000-0000-000000000000 is not a valid application identifier. |
| 700039 | 00000000-0000-0000-0000-000000000000 is not a valid resource identifier |
| 700040 | Managed Resource ID ‘{inputManagedResourceId}’ is not a valid resource identifier. |
| 700041 | Post-logout redirect uri is not in approved list. Requested post-logout url: {url}. |
| 700042 | The reply address does not match the reply addresses configured for the application. |
| 700043 | The redirect address ‘{address}’ does not match the redirect addresses configured for service identity ‘{serviceId}’. |
| 700044 | The redirect address ‘{address}’ corresponding to this authorization code does not match the redirect address ‘{requestAddress}’ specified in the request. |
| 700045 | Redirect address ‘{address}’ specified by the client does not match any configured addresses ‘{configuredAddress}’ or any addresses on the OIDC approve list. |
| 700046 | Invalid Reply Address. Reply Address must have scheme brk-{brkApplicationId}:// and be of Single Page Application type. |
| 700047 | Invalid Reply Address. Broker must use Single-Page Application Reply Address. |
| 700048 | Client assertion contains an invalid xms_actor_token claim. The audience of the claim is not correctly set. |
| 700049 | Claim override is only allowed for User Assigned Managed Service Identities. Make sure the caller app is a Managed Identity, and the override is being done for a User Assigned identity. |
| 700050 | Actor token is not within its valid time range. Current time: {curTime}, expiry time of actor token {expTime}. |
| 700051 | response_type ’token’ is not enabled for the application. |
| 700052 | The token request contains one or more unsupported response token type(s): ‘{ResType}’. |
| 700053 | response_type ‘id_token’ requires the ‘openid’ scope. |
| 700054 | response_type ‘id_token’ is not enabled for the application. |
| 700055 | Redirection to B2C first party app is permitted only to the /authresp endpoint. |
| 700056 | User account does not exist in organization. |
| 700081 | The refresh token has expired due to maximum lifetime. The token was issued on {issueDate} and the maximum allowed lifetime for this application is {time}. |
| 700082 | The refresh token has expired due to inactivity. The token was issued on {issueDate} and was inactive for {time}. |
| 700083 | The primary refresh token has expired due to maximum lifetime. The token was issued on {issueDate} and the maximum allowed lifetime for this application is {time}. |
| 700084 | The refresh token was issued to a single page app (SPA), and therefore has a fixed, limited lifetime of {time}, which cannot be extended. It is now expired and a new sign in request must be sent by the SPA to the sign in page. The token was issued on {issueDate}. |
| 900143 | ‘{name}’ is required for the ‘{type}’ grant type. |
| 900144 | The request body must contain the following parameter: ‘{name}’. |
| 900161 | Invalid access token. Required tenant ID claim is missing. |
| 900941 | Administrator consent is required. App is considered risky. |
| 900942 | Admin consent is required in order to allow token to be issued for clients to access resource. |
| 1000005 | Invalid definition for external identity provider, domain is missing |
| 1000006 | Invalid definition for external identity provider with domain ‘{domain}’. Reason: Following properties are mandatory: domain, issuer URI, passive authentication URL. |
| 1000007 | Invalid definition for external identity provider with domain ‘{domain}’. Reason: The value ‘{url}’ in the property ‘{urlType}’ must be an absolute URL. |
| 1000008 | Invalid definition for external identity provider with domain ‘{domain}’. Reason: The value ‘{url}’ in the property ‘{urlType}’ must be https. |
| 1000009 | Invalid definition for external identity provider with domain ‘{domain}’. Reason: Only WsFederation/SamlP/OAuth2 protocols are allowed. |
| 1000010 | Invalid definition for external identity provider with domain ‘{domain}’. Reason: Domain ‘{value}’ is not in expected format. |
| 1000011 | Invalid definition for external identity provider with domain ‘{domain}’. Reason: Issuer ‘{value}’ is not in expected format. |
| 1000012 | Invalid definition for external identity provider with domain ‘{domain}’. Reason: Domain ‘{value}’ is a reserved value. |
| 1000013 | Invalid definition for external identity provider with domain ‘{domain}’. Reason: Issuer ‘{value}’ is a reserved value. |
| 1000014 | Cannot issue On-Behalf-Of token for tenant ‘{tenant1}’ as JWT bearer token was issued for ‘{tenant2}’. |
| 1000015 | Direct federation users are not expected to have home tenant. |
| 1000018 | Realm with domain ‘{domain}’ is not an external realm. |
| 1000019 | The provided certificate authority type ‘{certificateAuthorityType}’ is not valid. |
| 1000020 | The provided application ‘{applicationId}’ may not be used on this endpoint. |
| 1000021 | External Claims Provider unavailable: general exception. |
| 1000022 | External Claims Provider unavailable: WebException status code ‘{status}’. |
| 1000023 | The GitHub access token forwarded exceeds the configured length of ‘{sizeLimit}’. |
| 1000024 | Requested claim ‘ClientIpReportedByRP’ should have a single and valid ip address. |
| 1000025 | Received invalid stk_jwk. |
| 1000026 | Received invalid Primary Refresh Token. |
| 1000027 | Session Transport Key is not present. |
| 1000028 | Received invalid Windows SSO Credential. |
| 1000029 | The provided confirmation request (req_cnf or pop_jwk) is not properly formatted. |
| 1000030 | Microsoft Account granted Refresh Token Credential is not supported on AAD tenant. |
| 1000031 | Application {appDisplayName} cannot be accessed at this time. Contact your administrator. |
| 1000032 | Received invalid stk_jwk key thumbprint. |
| 1000033 | Stk_jwk key doesn’t match session transport key thumbprint specified at the beginning of the session. |
| 1000034 | Stk_jwk key must not be submitted via x5c. |
| 1000035 | There was an error issuing Bound RT token. |
| 1000036 | BoundRT use as a bearer refresh token is unsupported. |
| 1000037 | Stk_jwk thumbprint is not provided for SSO Bound RT redemption. |
| 1000038 | Received invalid req_cnf key thumbprint. |
| 1000039 | Req_cnf key ‘{kid}’ doesn’t match proof of possession key thumbprint specified at the beginning of the session. |
| 1000040 | Received invalid dk_jwk key thumbprint. |
| 1000501 | Unable to read session document from Session Store. |
| 1000502 | The provided certificate is not within its specified validity window. |
| 1000503 | Request contains mismatched device ids. |
| 1002001 | The device template was not found in the tenant ‘{tenantName}’. |
| 1002002 | The Cert Based Auth Configuration was not found in the tenant ‘{tenantName}’ or was invalid. |
| 1002003 | The TLS certificate provided does not match the certificate on the device. |
| 1002004 | The MTLS subject was not found in the subject or SAN list. |
| 1002005 | Device in tenant ‘{tenantName}’ does not have suitable credentials. |
| 1002006 | Request contains empty or invalid subject. |
| 1002007 | Missing required roles to access token evaluation data endpoint, roles present in the token is {roles} |
| 1002008 | Unable to authorize to the token evaluation data endpoint. Tenant Identifier in the request: {requestTenant} does not match tenant identifier in the token: {tenantIdInToken} |
| 1002009 | Unable to authorize to the token evaluation data endpoint. Unexpected scope present in the bearer token, app delegation(service principal obo) token is not supported to access the endpoint. |
| 1002010 | There was an error on fetching revocaton data or issue with token evaluation data endpoint. |
| 1002011 | The tenant branding cdn domains are not configured for the private link. |
| 1002012 | The provided value for scope {scope} is not valid. Client credential flows must have a scope value with /.default suffixed to the resource identifier (application ID URI). |
| 1002014 | Unable to complete request. The request was invalid since domain_hint and opaque login_hint cannot be used together. |
| 1002016 | You are using TLS version 1.0, 1.1 and/or 3DES cipher which are deprecated to improve the security posture of Azure AD. Your TenantID is: {tenantId}. Please refer to https://go.microsoft.com/fwlink/?linkid=2161187 and conduct needed actions to remediate the issue. For further questions, please contact your administrator. |
| 1002017 | Bad Request. The passed logout_hint cannot be parsed. |
| 1002021 | The version of client library you are using is not supported for accessing resources in another Microsoft cloud as a guest. |
| 1002022 | A transient error occurred while attempting to fetch bloom filter data. Please try again later. |
| 1002023 | Invalid grant. Device authentication is required from a specific tenant. |
| 1002024 | A primary refresh token must be redeemed with a prt protocol version. |
| 1002026 | Common endpoint for app tokens is on the deprecation path and not supported on regional AAD. Please use the tenanted endpoint instead. |
| 1002027 | Some of the collected attributes were invalid. |
| 1002028 | Missing required roles to access partitioned token signing key endpoint, roles present in the token is {roles} |
| 1002029 | Unable to authorize to the partitioned token signing key endpoint. Unexpected scope present in the bearer token, app delegation(service principal obo) token is not supported to access the endpoint. |
| 1002030 | Internal service error occured in first party app token validator. |
| 1003012 | The custom extension returned an invalid action type defined for that custom extension type. |
| 1003013 | Invalid request. Nonce from artifact has expired. |
| 1003014 | The custom extension resourceId should be in the format of api://fully qualified domain name/appid. |
| 1003015 | The targetUrl and resourceId of the custom extension should have the same fully qualified domain name. |
| 1003016 | The appId of the custom extension resourceId should correspond to a real service principal in the tenant. |
| 1003017 | The Azure Active Directory Authentication Extensions service principal not found in tenant. |
| 1003018 | The Azure Active Directory Authentication Extensions service principal is disabled in this tenant. |
| 1003019 | The custom extension resource service principal is disabled in this tenant. |
| 1003020 | The target URL is in an improper format. It’s must be a valid URL that start with https:// |
| 1003021 | The permission CustomAuthenticationExtension.Receive.Payload is not granted to the service principal of the resource app. |
| 1003022 | The MS Graph service principal is disabled or not found in this tenant. |
| 1003023 | The endpoint used for the custom extension is blocked by the service. |
| 1003024 | The custom extension response size exceeded the maximum limit. |
| 1003025 | The total size of claims in the custom extension response exceeded the maximum limit. |
| 1003026 | The custom extension API responded with claims containing null or empty key. |
| 1003027 | Error connecting to the custom extension API. |
| 1003030 | A transient error occurred while authenticating an MSA (consumer) user. |
| 1003031 | Misconfigured required resource access in client application registration. |
| 1003032 | The bluestone storage account in TokenEvaluationData endpoint has not been successfully initialized |
| 1003033 | The remote ngc session was denied. |
| 1003034 | Your organization is not configured to sign in this type of personal Microsoft account. Visit https://aka.ms/MSAUnprotectedAccountsGuidance for more details. |
| 1003035 | The json web key supplied is invalid. |
| 1003036 | Partitioned token signing key feature is not set properly. |
| 1003037 | It looks like you may already have an account with us using this email address. Try signing in again with another identity provider. |
| 1003038 | Root token signing key is not found. |
| 1003039 | Partitioned token signing key is not found. |
| 5000611 | Symmetric Key Derivation Function version ‘{version}’ is invalid. |
| 5001210 | Unsupported transport key format. |
| 5001211 | Unable to create primary refresh token. |
| 5001212 | Device authentication is required to issue primary refresh token. |
| 5001213 | Windows Integrated authentication is needed. Unable to use Seamless SSO to authenticate the user. |
| 5001214 | Authentication failed. |
| 7000011 | Requested SAML 2.0 assertion has invalid SubjectConfirmation Method: {method}. |
| 7000012 | The grant was obtained for a different tenant. |
| 7000013 | The grant is not supported by API version {apiVersion}. |
| 7000014 | The provided value for the input parameter ‘device_code’ is not valid. |
| 7000015 | The grant was obtained for a different tenant. |
| 7000016 | Primary refresh token is not signed with session key. |
| 7000017 | Broker restricted refresh token can’t be used as credential. |
| 7000018 | Token binding header is empty. |
| 7000019 | Token binding hash does not match. |
| 7000020 | SAML 2.0 Bearer assertion must be a valid Base64Url encoded value. |
| 7000021 | Unrecognized grant type {type}. |
| 7000022 | VSM Binding Key missing from Ticket Granting Ticket request. |
| 7000023 | VSM Binding key mismatch. |
| 7000024 | Inconsistent broker application IDs asserted by incoming credentials. |
| 7000025 | Ambiguous request. The grant contains duplicate claims. |
| 7000026 | Provided grant is invalid or malformed. The grant requires an encrypted response, but the client is not indicating it understands encrypted responses. |
| 7000027 | An emergency refresh token is present but rejected. |
| 7000028 | Attestation key is required for this request but it doesn’t exist in the device. Please consider re-enrolling the device. |
| 7000029 | The token binding claim is invalid because it was not generated on the same device as attestation key. Please verify the legitimacy of the device. |
| 7000030 | The token binding claim is invalid because the thumbprint of binding key does not match the thumbprint in the binding claim or the thumbprint in the binding claim is missing. Please verify the legitimacy of the device. |
| 7000031 | The signing algorithm {algorithm} of attestation key is not supported. Please consider re-enrolling the device and update the attestation key. |
| 7000032 | The security enclave type {enclave} of the token binding key is unknown. Please consider re-enrolling the device. |
| 7000033 | Token doesn’t contain expected claim: ‘{claim}’. |
| 7000034 | The token binding claim is malformatted. Please consider re-enrolling the device. |
| 7000110 | Request is ambiguous, multiple application identifiers found. |
| 7000112 | Application ‘{appIdentifier}’({appName}) is disabled. |
| 7000113 | Application ‘{appIdentifier}’ is not authorized to make application on-behalf-of calls. |
| 7000114 | Application ‘{appIdentifier}’ is not allowed to make application on-behalf-of calls. |
| 7000115 | This grant is reedemable only by broker application. |
| 7000116 | Client application ‘{appIdentifier}’({appName}) is disabled in tenant {tenant}. Please review the documentation: https://go.microsoft.com/fwlink/?linkid=2167553 |
| 7000117 | Resource application ‘{appIdentifier}’({appName}) is disabled in tenant {tenant}. Please review the documentation: https://go.microsoft.com/fwlink/?linkid=2167553 |
| 7000210 | Unable to find source of Trusted Certificate Authority policy. |
| 7000211 | Trusted Certificate Authority policy is not configured on the tenant ‘{tenantId}’. |
| 7000212 | No matching Trusted Certificate Authority policy found for authorized subject name. |
| 7000213 | Invalid certificate chain. |
| 7000214 | Certificate has been revoked. |
| 7000215 | Invalid client secret provided. Ensure the secret being sent in the request is the client secret value, not the client secret ID, for a secret added to app ‘{identifier}’. |
| 7000216 | ‘client_assertion’, ‘client_secret’ or ‘request’ is required for the ‘client_credentials’ grant type. |
| 7000217 | The service principal named {appPhrase} was not found in the tenant named {tenant_name}. This can happen if the application has not been installed by the administrator of the tenant. |
| 7000218 | The request body must contain the following parameter: ‘client_assertion’ or ‘client_secret’. |
| 7000219 | ‘client_assertion’ or ‘client_secret’ is required for the ‘{type}’ grant type. |
| 7000220 | Client application identifier in the provided grant doesn’t match ‘client_id’ parameter. |
| 7000221 | Certificate Subject must match Issuer claim in the client assertion. |
| 7000222 | The provided client secret keys for app ‘{identifier}’ are expired. Visit the Azure portal to create new keys for your app: https://aka.ms/NewClientSecret, or consider using certificate credentials for added security: https://aka.ms/certCreds. |
| 7000223 | Application {brokerAppId} is not authorized to broker tokens. |
| 7000224 | Application {childAppId} is not authorized to have tokens brokered on its behalf. |
| 7000225 | Invalid credentials: An MSI certificate was included in the request for the app, but the app (object ID: {oid}, application id: {clientId}) is not an MSI. Ensure that your code is matching MSI identities and certificates appropriately. |
| 7000226 | No federated identity credential policy found on application ({appid}). The client_assertion used to authenticate the request does not match the subject or application being requested. Ensure that the application ID in the request is correct, that the app has a policy applied to it, and that the correct client_assertion is being provided in the request. |
| 7000227 | No Federated Identity Credential policy found on application that matched the presented MSI-signed client assertion. Expecting a Federated Identity Credential with subject: ‘{msiSpid}’, issuer: ‘{expectedIssuer}’ and audience: ‘{expectedAudience}’. |
| 7000228 | Application {brokerAppId} is not authorized to broker tokens. |
| 7000229 | The client application {appId} is missing service principal in the tenant {tenantId}. See instructions here: https://go.microsoft.com/fwlink/?linkid=2225119 |
| 9002310 | Invalid request. The transforms element must contain at least one transform. |
| 9002311 | Invalid request. Unsupported canonicalization algorithm. |
| 9002312 | Invalid request. XML is empty. |
| 9002313 | Invalid request. Request is malformed or invalid. |
| 9002314 | Resource hostname is required. |
| 9002315 | Invalid request. Cannot use /consumers/ on v1 signout. |
| 9002316 | Invalid request. Cannot select consumer user session if the endpoint does not support consumer logout. |
| 9002317 | Invalid issuer specified. |
| 9002318 | Invalid request. Cannot select consumer user session and enterprise user session at the same time. |
| 9002319 | Public clients can’t send a client secret. |
| 9002320 | The realm ‘{realm}’ is not a configured realm of the tenant. |
| 9002321 | No credentials found with the necessary validated claims that map to external user information. |
| 9002322 | Protected forwarded token request is not in correct format. |
| 9002323 | Certificate must be a valid base64 encoded certificate. |
| 9002324 | Request should not contain more than one client credential parameters, this includes ‘client_secret’, ‘client_assertion’ and ‘request’ parameters. |
| 9002325 | Proof Key for Code Exchange is required for cross-origin authorization code redemption. |
| 9002326 | Cross-origin token redemption is permitted only for the ‘Single-Page Application’ client-type. Request origin: ‘{origin}’. |
| 9002327 | Tokens issued for the ‘Single-Page Application’ client-type may only be redeemed via cross-origin requests. |
| 9002328 | Invalid request. Cannot use /common or /consumers on admin-consent. Please specify the tenant in GUID or friendly name format OR generically reference it with /organizations. |
| 9002329 | Misconfigured client or resource Service Principal ‘{appId}’. Missing Salt Key. |
| 9002330 | Invalid Request. Wam_compat version is not supported. |
| 9002331 | Application ‘{principalId}’({principalName}) is configured for use by Microsoft Account users only. Please use the /consumers endpoint to serve this request. |
| 9002332 | Application ‘{principalId}’({principalName}) is configured for use by Azure Active Directory users only. Please do not use the /consumers endpoint to serve this request. |
| 9002333 | Invalid request. The RDP request is missing the PoP key via req_cnf. |
| 9002334 | Invalid request. The RDP logon request is missing the RDP assertion. |
| 9002335 | Invalid request. The RDP assertion is invalid or is missing mandatory properties. |
| 9002336 | Invalid RDP request. |
| 9002337 | Invalid request. The application is registered in the legacy Microsoft Account tenant using apps.dev.microsoft.com, but is configured for use by Azure Active Directory tenants only. Use of /common is not supported for this registration. Please use a tenanted endpoint to request a token. |
| 9002338 | Invalid request. Request is malformed or invalid. |
| 9002339 | Unsupported user account for this endpoint. The user is a Microsoft Accounts user, but this app does not have the Microsoft account audience enabled. Either enable Microsoft account support to use the /common endpoint or use the tenanted endpoint to target a specific Azure AD tenant for auth. |
| 9002340 | The permission (scope) list {scopeListString} is missing Rdp flow allowed permissions. |